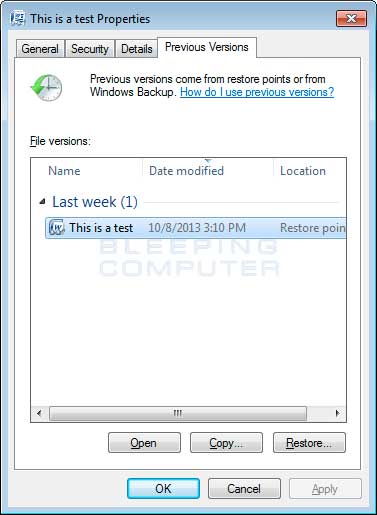
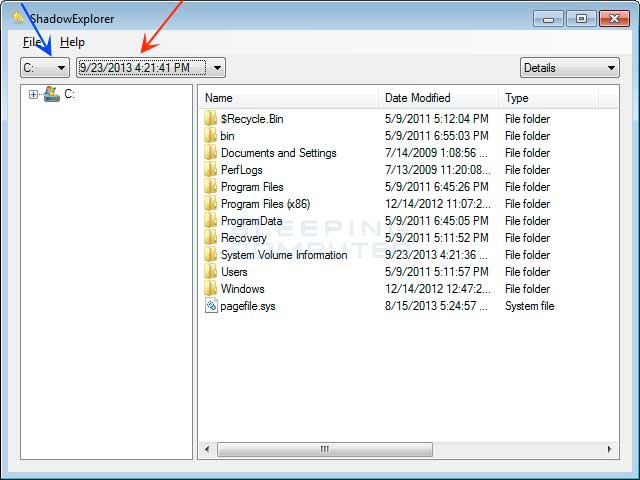
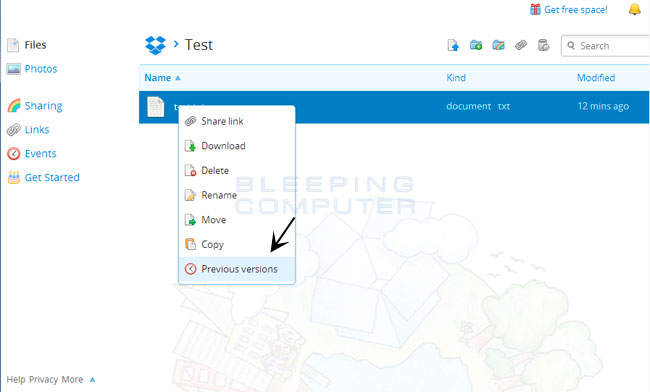
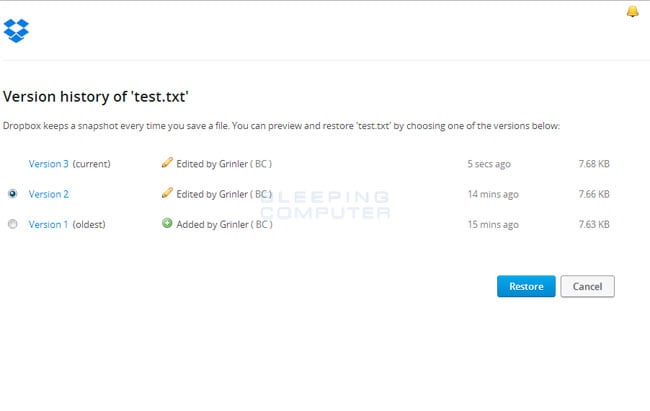
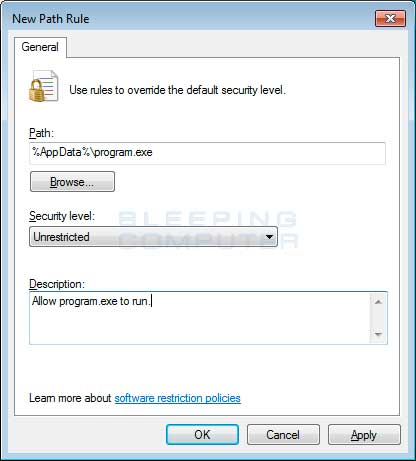
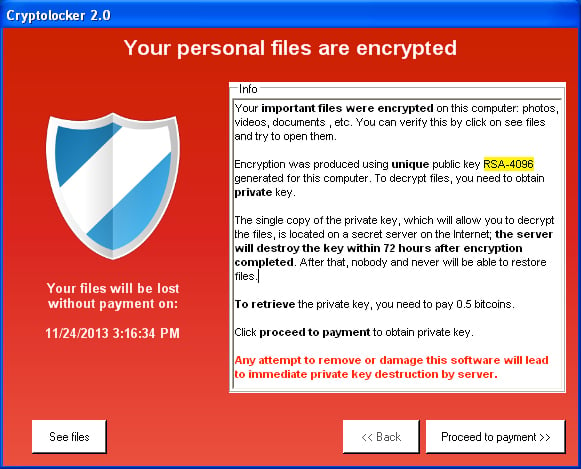
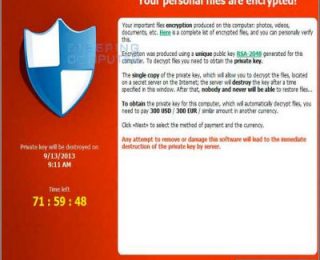
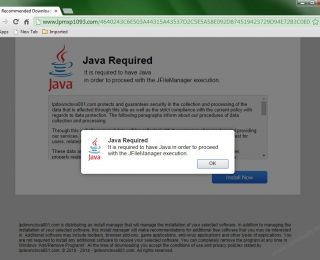
- Uygulama
- Blog+18 Android Android market Oyunlar Uygulamalar Araçlar 2D/3D Çizim Ajanda/Hatırlatma Bakım- Onarım Çeşitli Araçlar Donanim Sürücüleri Dosya Araçları Eğlence Pdf Araçları Pratik Araçlar Program Kaldırıcılar Resim Düzenleme Programları Sıkıştırma -Yedekleme Sistem Araçları sozluk Veri Kurtarma Video ve Müzik Yardımcı Araçlar Zamanlayıcılar Bilgisayar Oyunları Aksiyon Eğlence Blog Yazılım Chrome Çocuk Eğitici eKitap dini teknoloji Finans firefox Google Güvenlik Anti Spyware Programları Antivirüs Programları Çeşitli Güvenlik Programları indir İnternet Araçları eposta İndirme Programları Tarayıcı Eklentileri Tarayıcılar İOS Oyunlar Uygumalalar Kampanyalar Linux Mac Mobil Cihazlar araçlar eğitim eğlence finans Güvenlik haberleşme iş müzik ve ses Oyunlar Aksiyon yarış Senkrizasyon Programları Sosyal Sosyal Medya Uygulamalar verimlilik Video Muhasebe / Ofis Excel Programları Muhasebe Programları Ticari & Ofis Öğrenci ve Eğitim Eğitim Programları Hesaplama ve Dönüştürme Öğrenci Programları Programlama Masaustu Wordpress Teknoloji Haberleri Videolar Windows Phone WindowsPhone Uygulamaları YandexMIUI Reklamlarından Kurtulma Yolları
28/03/2019
Bad Rabbit Nedir Nasıl Kaldırılır ?26/10/2017
Sony Channel Frekans Bilgileri31/03/2017
- Teknoloji Haberleri
- VideoEkran Kaydedici Uygulaması
19/07/2019
Tik Tok – including musical.ly Apk14/08/2018
Cameos on Google İndir ios13/08/2018
YouTube Go Apk indir08/02/2018
VMate indir17/11/2017
Vidme Apk indir21/10/2017
- Bize Ulaşın